Inside a global leader in CyberSecurity [bitdefender dashboard]

Intro:
While ago I have discovered a blind cross-site-scripting that allowed me to access the bitdefender administrator’s dashboard a Czech Republic bitdefender’s domain., with plenty of functionalities, and this is how it went:
So, the vulnerability is named blind for purpose :). The injected js is loaded outside the actual user session (in most cases), and it does render inside some admin dashboard, or any other areas where the injected input wasn’t sanitized before it’s rendered! when I had received the callback from the xss hunter report, I immediatly (to be honest, it was late and decided to check it the other day) requested the same url domain/admin, and tried to impersonate the admin session, and horray I’m in !
Starting from the end:
This is the flashback of the results caused by the underlining issue:
-
My PoC using the dashboard in question:
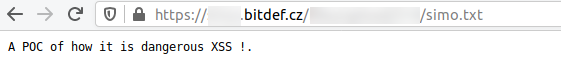
Reported PoC -
Bitdefender Administrator’s Dashboard:
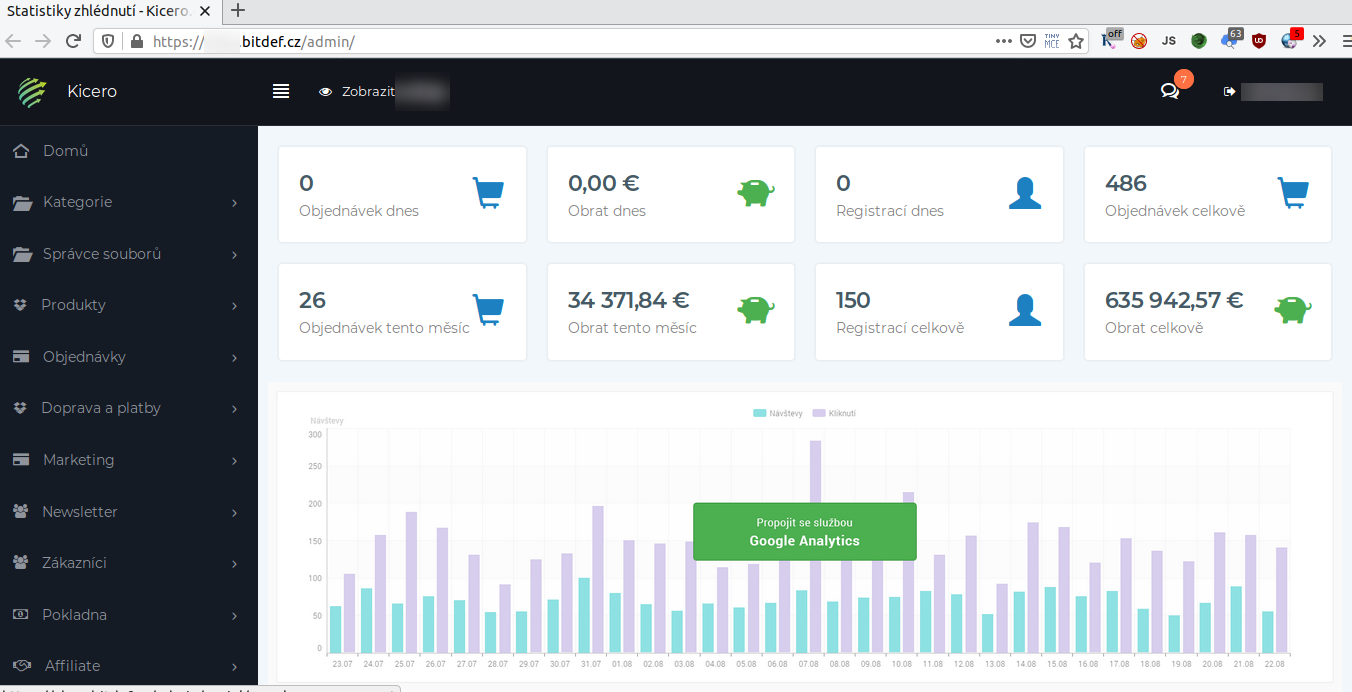
Bitdefender Dashboard1 -
Bitdefender sells :), some money !
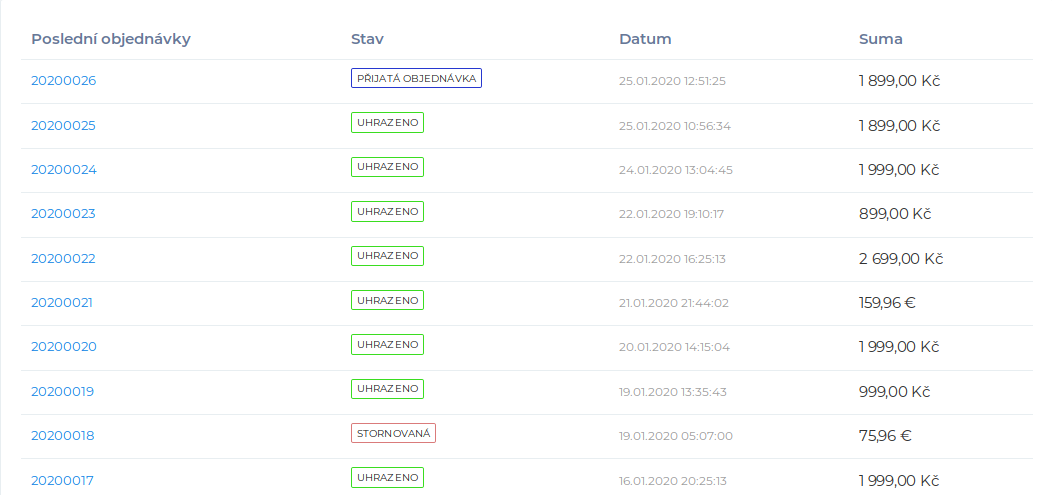
Bitdefender Dashboard2 -
Bitdefender Admin Cookies :
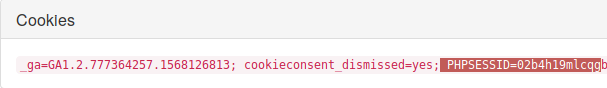
Bitdefender admin’s session -
Xss hunter report:
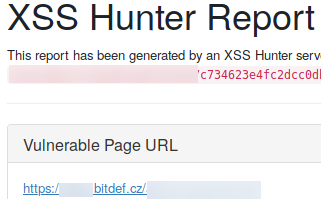
Xss hunter report
Sessions are meant to be distroyed:
The “main” raison that let me use the admin’s session cookies, is simply they weren’t revoked at all(it’s an issue in itself) and thus allow anyone with the right cookies to get in. Besides, no httpOnly flag was set on cookies that could restrict them from being stolen. As a takeaway, and for safety raison any time you used a “web” application and you are done with it, just simply log out, and don’t keep your sessions valid, as some of the apps doesn’t revoke them automatically!
Final note: (to self) :grimacing:
-
Sometimes even if the input seems to be sanitized, and the payload rendered html encoded for instance, just make sure to test it again and mark that input and wait !
-
Never underestimate a client side bug ! and just test for them. (don’t be that lazy).
NB:
Nothing was retrieved from the server. The issue was fixed by the bitdefender team.