Fear the EAR Vuln
Fear the EAR (Exit After Redirect) is a simple yet often overlooked vulnerability that can allow authentication bypass. This short post walks through the discovery process, how I exploited the issue, and how it was responsibly reported back to the program. Read more

![Struts your way into Strongkey [RCE]](/images/c3Ryb25na2V5LXJjZQo=.png)
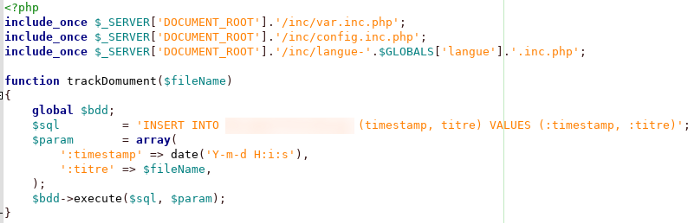
![Inside a global leader in CyberSecurity [bitdefender dashboard]](/images/Ynhzcy1iaXRkZWZlbmRlcgo=.png)
