A story of how I exploited a forgotten attack vector to easily achieve maximum vulnerability impact on a big company
Read more
Fear the EAR (Exit After Redirect) is a simple yet often overlooked vulnerability that can allow authentication bypass. This short post walks through the discovery process, how I exploited the issue, and how it was responsibly reported back to the program.
Read more
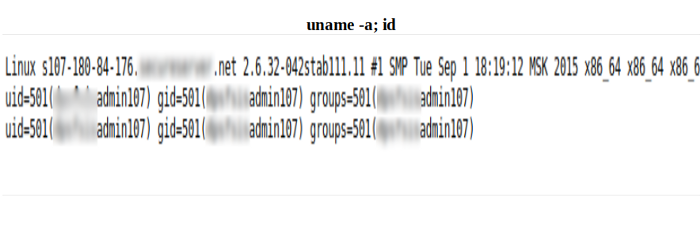
Here's how I could pwned StrongKey, while exploiting an already released patch CVE. And this is why it's important to keep your component updated !
Read more
Local file include can be used by developers to retrieve files in the current working directory, however when an attacker locate the vulnerable endpoint, he can jump directories to read sensitive system files And this what happens when I was conducting my usual academic work till observing this LFI !
Read more
In this post, I describe how I was able to access the internal administrator dashboard of one of the well-known antivirus softwares (Bitdefender) by exploiting a blind xss and session hijacking.
Read more
A writeup about a finding that exploits an endpoint in an embedded javascript code, that leads to Account Takeover, then using the admin dashboard to get RCE !
Read more

![Struts your way into Strongkey [RCE]](/images/c3Ryb25na2V5LXJjZQo=.png)
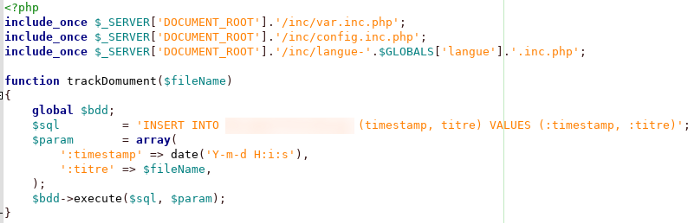
![Inside a global leader in CyberSecurity [bitdefender dashboard]](/images/Ynhzcy1iaXRkZWZlbmRlcgo=.png)